
While working on Linux Operating system, one definitely came across a stage, where we have to perform some troubleshooting, which is not possible without Single user mode (ex: Resetting forgotten root password, fixing filesystem issues etc).
Single user mode (aka Maintenance Mode) is a mode in which a multi-user computer operating system boots into a single superuser. It is mainly used for maintenance of multi-user environments such as network servers. Some tasks may require exclusive access to shared resources.
It is runlevel 1 under system SysV init, and runlevel1.target or rescue.target in systemd.
BOOTING SYSTEM IN SINGLE USER MODE
1) Boot(Restart) your system and wait until the GRUB2 menu appears.
2) In the boot loader menu, select your kernel version entry and press e to edit.
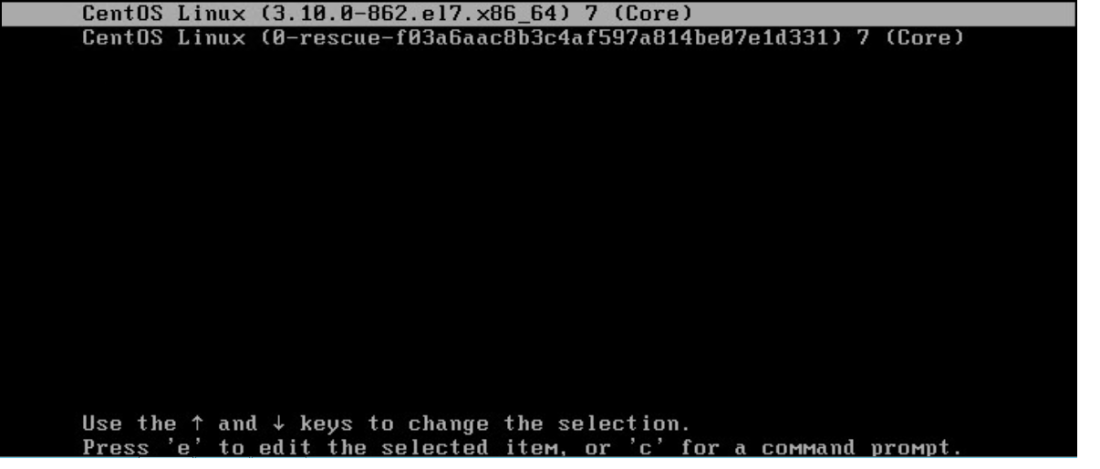
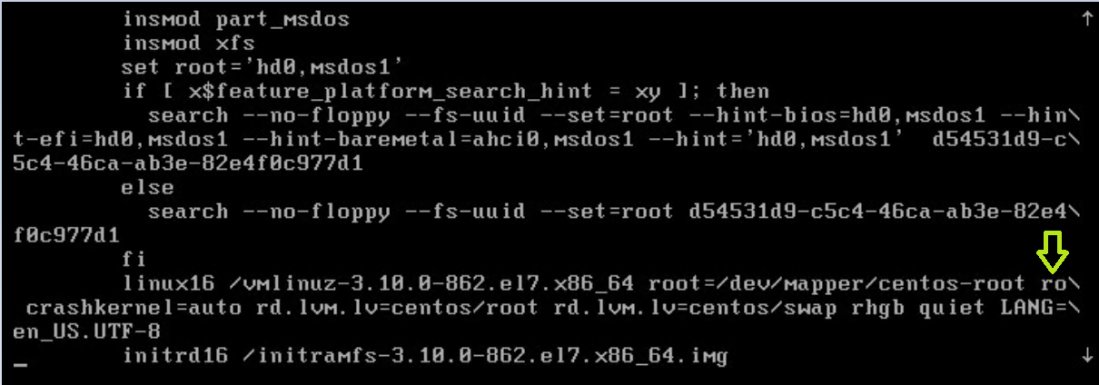
3) Find the line beginning with linux16. At the end of this line, append the following: replace “ro” with “rw init-/sysroot/bin/sh”.
Before conversion
After conversion
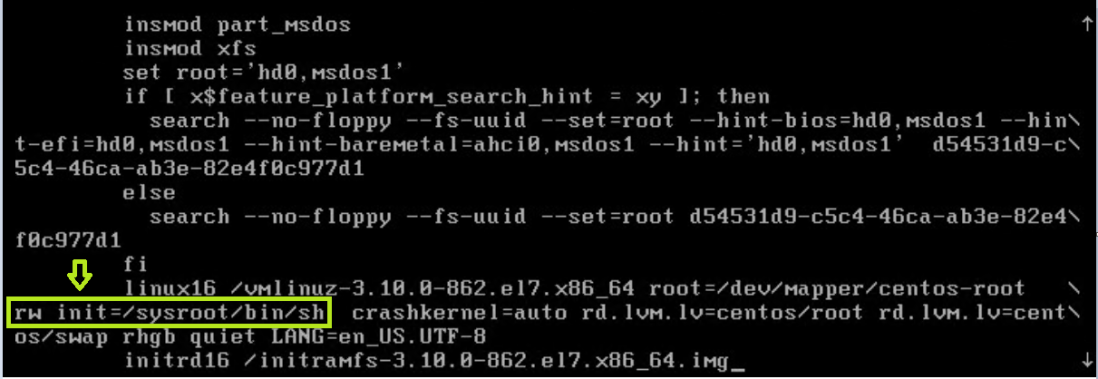
Press F10 or Ctrl+X to boot the system using the options you just edited (access an emergency shell).
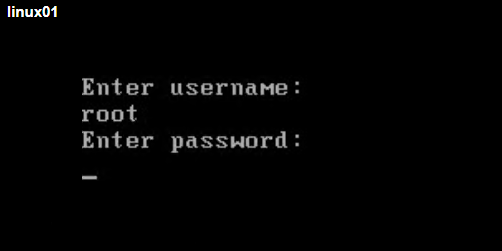
4) Once the system boots, you will be presented with a shell prompt without having to enter any user name or password:
Mount root filesystem temporarily
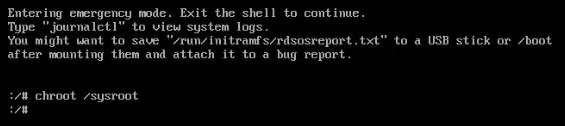
Perform tasks as per the requirements (as we are changing root password here)
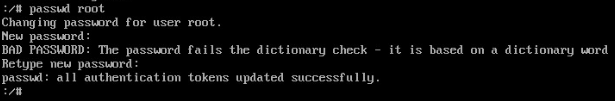
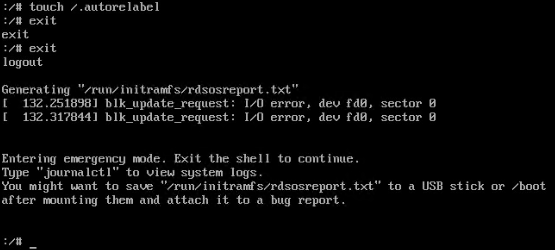
5) Once you are done with changes, instruct SELinux to relabel all files upon reboot (because the /etc/shadow file was changed outside of its regular SELinux context) — run:
SETTING PASSWORD ON EDITING KERNEL ENTRY
Password is required for modifying menu entries but not for booting existing menu entries:
1) Run the grub2-setpassword command as root:
[root@linux01 ~]# grub2-setpassword
Enter password: redhat
Confirm password: redhat
[root@linux01 ~]#
2) Following this procedure creates a /boot/grub2/user.cfg file that contains the hash of the password.
[root@linux01 ~]# cat /boot/grub2/user.cfg
GRUB2_PASSWORD=grub.pbkdf2.sha512.10000.51E60744B2E6EE55687FFE5D0C495961E39840FE8B66F1BDBE38B69CA64B02D66071DC7FF6F69340721C6B49F62B02156DD1223F07C01B7AEAF5CB1DA7DA81CD.BB2CAE35A896A606816318705B6BEEB2D874ACAFF53ECA98E306A2E8FDF694C96BC56572B44CC01B828ED181B05C4468A25A72B9A1B3398A6D9B4A8BEE20F103
[root@linux01 ~]#
3) The user for this password, root, is defined in the /boot/grub2/grub.cfg file. With this change, modifying a boot entry during booting requires you to specify the root user name and your password.
SETTING PASSWORD TO SECURE GRUB ITSELF (RHEL7.2 or above)
Setting a password using the grub2-setpassword prevents menu entries from unauthorized modification but not from unauthorized booting. To also require password for booting an entry, follow these steps after setting the password with grub2-setpassword:
1) Open the /boot/grub2/grub.cfg file.
2) Find the boot entry that you want to protect with password by searching for lines beginning with menuentry.
[root@linux01 ~]# cat /boot/grub2/grub.cfg | grep -i unrestricted
menuentry ‘CentOS Linux (3.10.0-862.el7.x86_64) 7 (Core)’ –class centos –class gnu-linux –class gnu –class os –unrestricted $menuentry_id_option ‘gnulinux-3.10.0-862.el7.x86_64-advanced-00d34b55-6ba1-4e12-b74b-aa5a4b43c4ea’ {
menuentry ‘CentOS Linux (0-rescue-f03a6aac8b3c4af597a814be07e1d331) 7 (Core)’ –class centos –class gnu-linux –class gnu –class os –unrestricted $menuentry_id_option ‘gnulinux-0-rescue-f03a6aac8b3c4af597a814be07e1d331-advanced-00d34b55-6ba1-4e12-b74b-aa5a4b43c4ea’ {
3) Delete the –unrestricted parameter from the menu entry block, save and close the file
[root@linux01 ~]# vi /boot/grub2/grub.cfg
[root@linux01 ~]# cat /boot/grub2/grub.cfg | grep -i unrestricted
menuentry ‘CentOS Linux (0-rescue-f03a6aac8b3c4af597a814be07e1d331) 7 (Core)’ –class centos –class gnu-linux –class gnu –class os –unrestricted $menuentry_id_option ‘gnulinux-0-rescue-f03a6aac8b3c4af597a814be07e1d331-advanced-00d34b55-6ba1-4e12-b74b-aa5a4b43c4ea’ {
[root@linux01 ~]#
NOTE:If you delete the –unrestricted parameter from every menu entry in the /boot/grub2/grub.cfg file, all newly installed kernels will have menu entry created without –unrestricted and hence automatically inherit the password protection.

Note: Manual changes to the /boot/grub2/grub.cfg persist when new kernel versions are installed, but are lost when re-generating grub.cfg using the grub2-mkconfig command. Therefore, to retain password protection, use the above procedure after every use of grub2-mkconfig.

Utterly composed articles , thankyou for selective information .
LikeLiked by 1 person
Thank you lucien for your feedback
LikeLike
Hey, you used to write great, but the last few posts have been kinda boring… I miss your great writings. Past few posts are just a bit out of track! come on!
LikeLiked by 1 person
Hi John,
Thanks for your feedback, we are trying to update more content so hopefully you will find it good. Still if you have any topics in mind feed free to suggest and we will try to write on it.
LikeLike
Whats up very cool site!! Man .. Beautiful .. Superb .. I’ll bookmark your blog and take the feeds also…I am satisfied to seek out a lot of helpful information here within the post, we need develop more techniques on this regard, thanks for sharing.
LikeLike
Thanks Paul for the motivating comments
LikeLike
I dugg some of you post as I cerebrated they were very helpful very useful
LikeLike
You have brought up a very superb details , thanks for the post.
LikeLike
Welcome lila
LikeLike
Very neat blog post.
LikeLike
Thanks for sharing, this is a fantastic blog article.Really looking forward to read more. Awesome.
LikeLike
I really like and appreciate your blog post.Really thank you! Keep writing.
LikeLike
Appreciate you sharing, great article post.Really thank you! Great.
LikeLike
Im grateful for the post. Want more.
LikeLike
Thanks you, surely new content will be uploaded soon
LikeLike
Hey, thanks for the blog. Cool.
LikeLike
Thanks again for the article.Really thank you! Awesome.
LikeLike
Major thankies for the article post.Thanks Again. Really Great.
LikeLike
Looking forward to reading more. Great article.Much thanks again. Really Great.
LikeLike
I loved your article post. Much obliged.
LikeLike
Thanks a lot for the blog post. Fantastic.
LikeLike
Really appreciate you sharing this blog.Really thank you! Want more.
LikeLike
Thanks again for the article.Thanks Again. Fantastic.
LikeLike
Im grateful for the blog.Thanks Again. Want more.
LikeLike
“This site was… how do you say it? Relevant!! Finally I’ve found something that helped me. Cheers!”
LikeLike
Very good blog article. Cool.
LikeLike
Hey, thanks for the post.Really looking forward to read more. Great.
LikeLike
Really appreciate you sharing this blog article. Really Great.
LikeLike
“We absolutely love your blog and find nearly all of your post’s tobe exactly I’m looking for. can you offer guest writers to write content in your case?I wouldn’t mind writing a post or elaborating on a few of the subjects you write withregards to here. Again, awesome web site!”
LikeLike
I’m still learning from you, while I’m improving myself. I definitely enjoy reading everything that is posted on your site.Keep the stories coming. I liked it!
LikeLike
Awesome article post. Want more.
LikeLike
I am not positive the place you will be having your information, but great topic. I has to spend a little while studying more or finding out more. Many thanks for fantastic information I was once on the lookout for this information for my mission.
LikeLike
Very great post. I just discovered your weblog and wished to express that I’ve really loved surfing around your weblog posts. In the end I am going to be subscribing on your feed and I’m hoping you write again very soon!
LikeLike
This is really interesting, You are a very skilled blogger. I’ve joined your feed and look forward to seeking more of your fantastic post. Also, I have shared your web site in my social networks!
LikeLike
As the admin of this website is working,
no hesitation very shortly it will be renowned, due to its quality contents.
Feel free to surf to my web-site: Cake Recipe Book For Kids
LikeLike
Well I use mobile friendly theme from WordPress store
LikeLike
I’m not sure why but this weblog is loading extremely slow for me.
Is anyone else having this issue or is it a issue
on my end? I’ll check back later on and see if the problem still exists.
Also visit my web site: RickLBuemi
LikeLike
I appreciate you sharing this article post.Thanks Again. Much obliged.
LikeLike
Hey very cool website!! Man .. Excellent .. Amazing .. I will bookmark your site and take the feeds also…I am happy to find so many useful info here in the post, we need work out more techniques in this regard, thanks for sharing. . . . . .
LikeLike
Good site you have here.. It’s difficult to find excellent writing like yours these days. I truly appreciate people like you! Take care!!
LikeLike
Good post. I learn something totally new and challenging on sites I stumbleupon everyday. It will always be interesting to read through articles from other authors and practice something from their web sites.
LikeLike
Having read this I believed it was very enlightening. I appreciate you finding the time and energy to put this content together. I once again find myself personally spending a significant amount of time both reading and commenting. But so what, it was still worth it!
LikeLike
Im obliged for the blog.Really looking forward to read more. Much obliged.
LikeLike
Hmm it seems like your blog ate my first comment (it was extremely long) so I guess I’ll just sum it up what I submitted and say, I’m thoroughly enjoying your blog. I too am an aspiring blog blogger but I’m still new to the whole thing. Do you have any tips for inexperienced blog writers? I’d definitely appreciate it.
LikeLike
I am usually to blogging we actually appreciate your articles. This content has really peaks my interest. I am about to bookmark your blog and keep checking for brand spanking new data.
LikeLike
Looking forward to reading more. Great blog.Really looking forward to read more. Fantastic.
LikeLike